Examining the Trend of 0-Day Vulnerabilities in 2024

I recently came across a podcast with Phil Venables, Google Cloud's CISO. In this podcast he spoke about the recent Google Threat Intelligence Report released. I'm always interested in cybersecurity trends, so I gave it a quick read. This short blog will go over some of my favourite key points from the 19 page document.
The podcast and the Report can be found at the bottom.
Context
0-Day Vulnerability - A vulnerability that was maliciously exploited in the wild before a patch was made publicly available.
All facts, and figures are directly from the Google Threat Intelligence Report. The report covers trend data relating to 0-Day vulnerabilities. Google claims that all data was collected by themselves and other open source repositories.
This won't cover the undiscovered 0-Day vulnerabilities for self-explanatory reasons.
Number of 0-Day Vulnerabilities in 2024
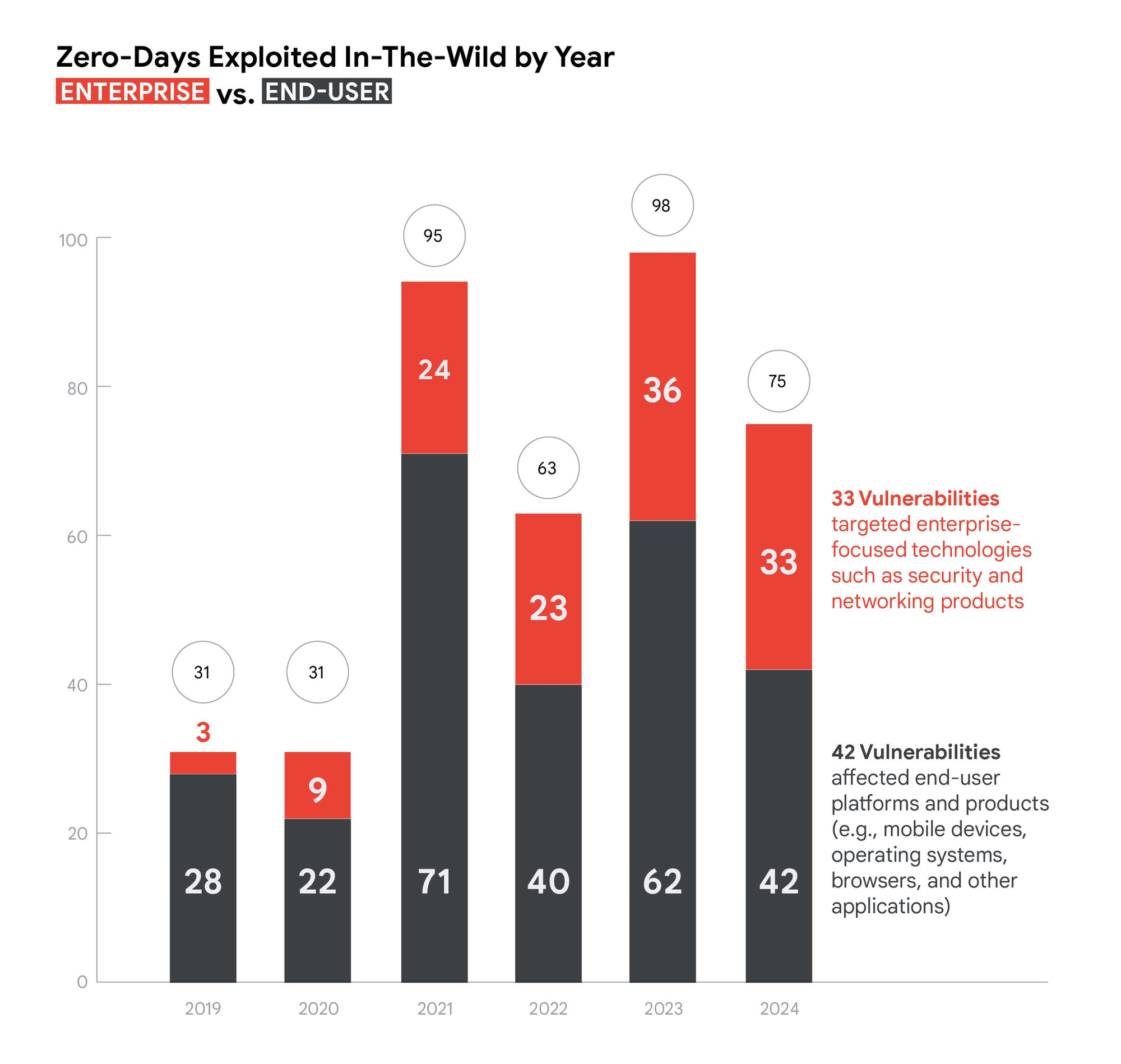
In 2024 we saw a decrease in total reported 0-Day vulnerabilities from 2023, however, if we look at it from a holistic view, we continue to see an upward trend for 0-Day vulnerabilities since 2019.
Whilst the most common 0-Day vulnerabilities targeted software typically used by end-users, the coverage of enterprise-focused vulnerabilities rose from 37% in 2023, to 44% in 2024.
End-User Products and Platforms Coverage
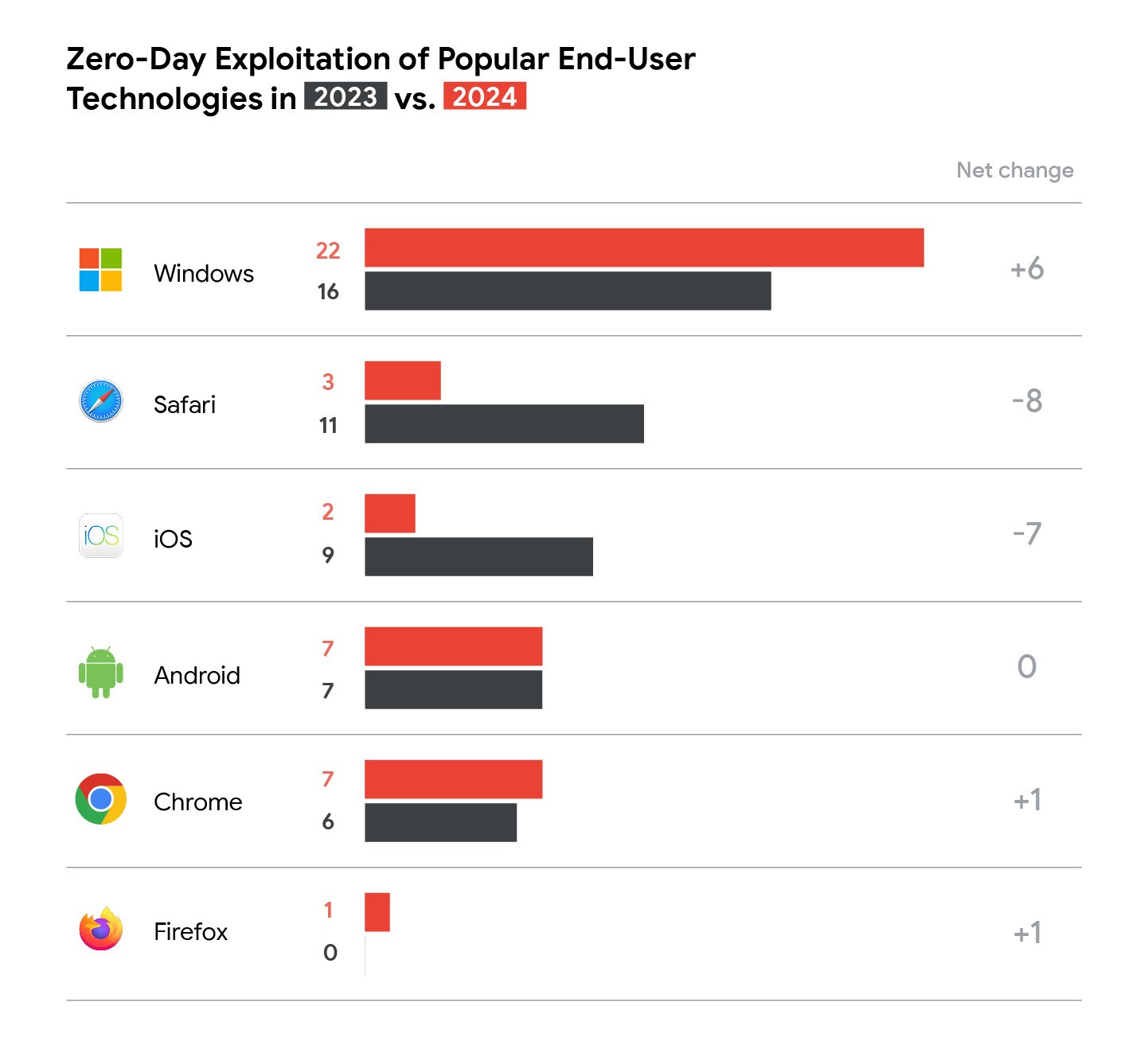
In the number of reported 0-Day vulnerabilities for End-User products and platforms, Apple's iOS and Safari had a significant decrease in vulnerabilities found in comparison to 2023.
Windows however, had a significant increase in the number of 0-Day vulnerabilities found. With Android, and Chrome staying pretty stagnant.
From the above results, the most popular targets of 0-Day vulnerabilities are Operating Systems and Web Browsers.
0-Day vulnerabilities are hard to defend against, however, by segmenting your network, and minimising the impact of a potential breach, you are decreasing the significance of an attack.
Enterprise Technologies
As mentioned previously, the proportion of vulnerabilities coming from Enterprise Technologies increased from 37% to 44% between 2023 and 2024.
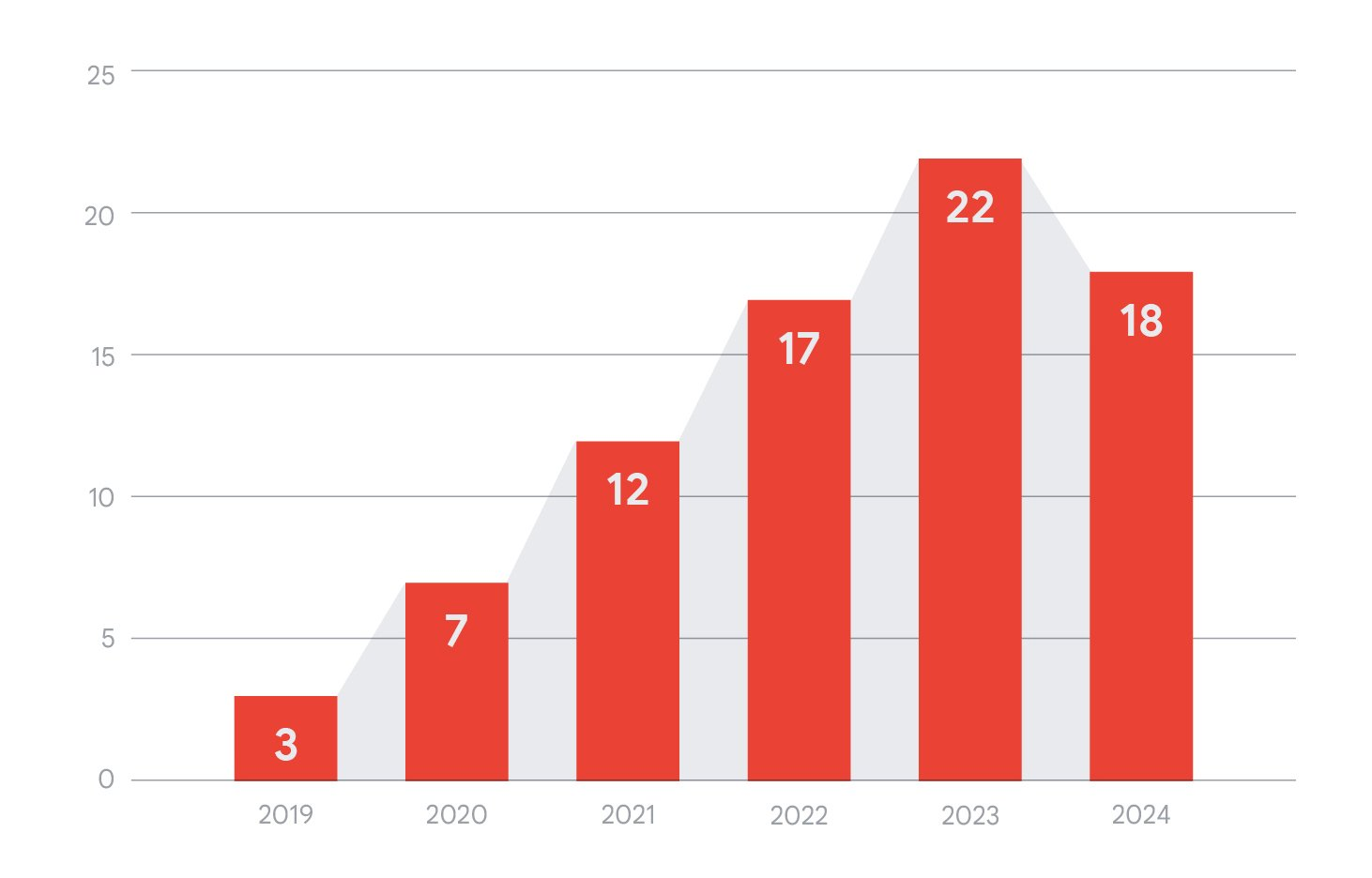
There has also been a gradual increase in the number of unique enterprise vendors targeted (although it did slightly go down in 2024).
Who Is Driving Exploitation?
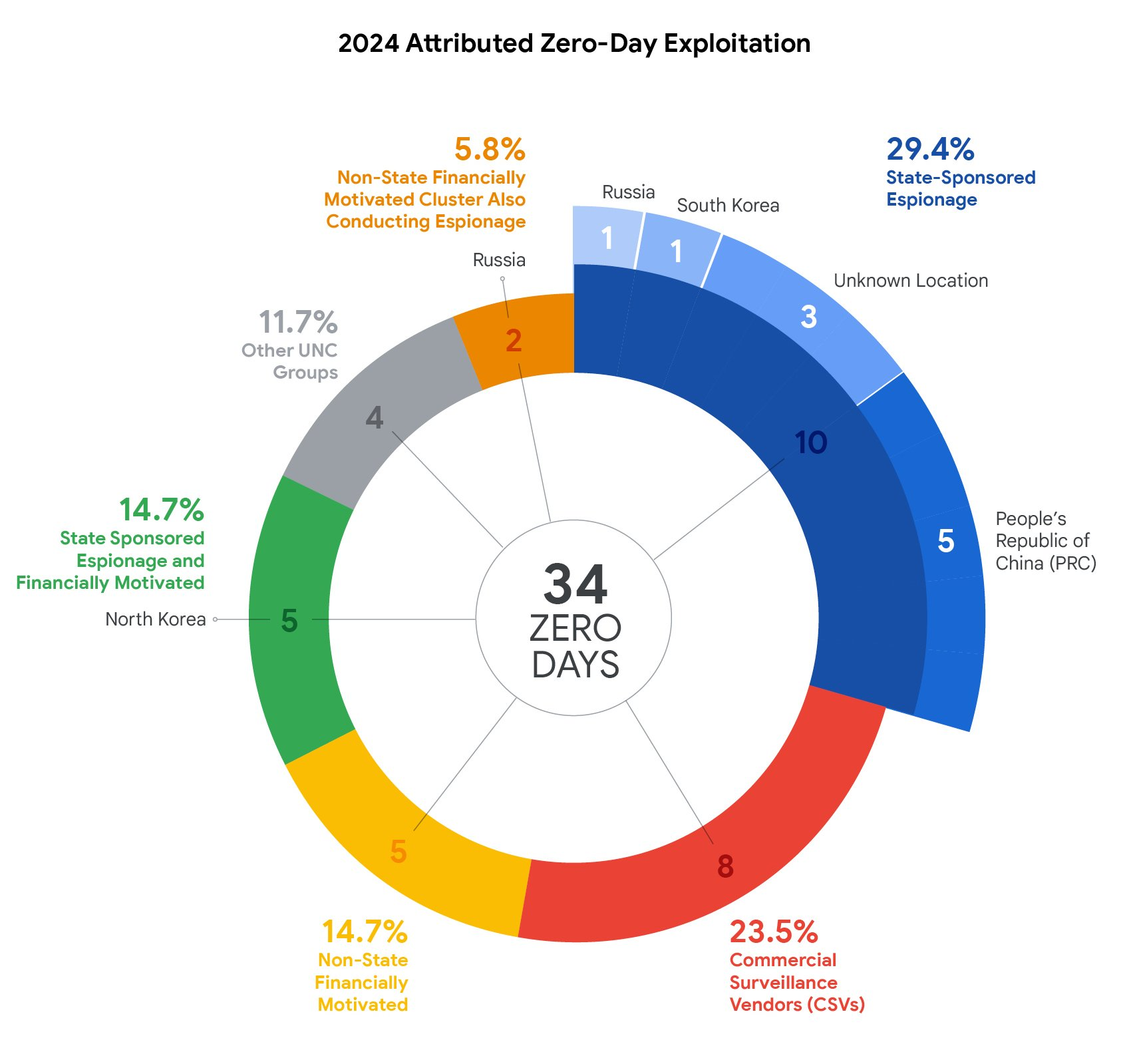
Only 34 0-Day vulnerabilities could be attributed to a category.
The most popular reason for exploiting 0-Day vulnerabilities came from state-sponsored espionage, with China leading it, followed by South Korea, and Russia. Some attacks were able to mask their origin and therefore could not be properly attributed.
Commercial Surveillance Vendors (CSVs) took up the number 2 spot, with Non-State, financially motivated groups coming in third place.
No surprise coming from North Korea with State-Sponsored Espionage and Financially Motivated crimes coming fourth. If you want an interesting video on how North Korea finances their regime using cyberwarfare, I'll link it below in the resources section.
Conclusion
It is no surprise to see the increase in 0-Day Vulnerabilities if we compare it to where it was in 2019. 0-Day vulnerabilities are critical resources that can be used to gain access to devices, intellectual property, and money.
I don't see the growth stopping either. As AI improves, discovery of 0-Day vulnerabilities will be facilitated. Furthermore, as we enter a new era of militarisation, I will not be surprised to see more governments getting involved in this area, not just your typical culprits.
I would encourage anyone who is interested 0-day vulnerabilities or in a leadership position to read the full Google Threat Intelligence Report to understand the current threat landscape, at least from a 0-Day perspective. The report contains more detailed analysis on data shown, other data (most popular vulnerabilities), and complete breakdowns of popular 0-Day vulnerabilities from last year.
Resources Mentioned
- Phil Venables Shift Down Not Left Podcast
- Google Threat Intelligence Report
- How North Korea Finances it's Regime using Cyberwarfare




