Security Diaries #4

The Impact of AI on the Cybersecurity Workforce
In June 2025, NIST updated its NICE Framework to include new areas related to AI. If you’re not familiar with NICE, it’s a resource designed to help employers hire and develop their security workforce. It outlines different types of teams, roles, responsibilities, and the competencies those teams need to build. It’s also a great resource if you’re looking to upskill, since it provides guidance tailored to each role.

They added AI as a new competency area. "It covers the foundational knowledge and skills needed to understand the intersection between AI and cybersecurity, and the risks and opportunities it may present". As AI continues to develop, it becomes more and more important for the workforce to have a foundational understanding as to how AI works, and what they can do with it.
They also mentioned that AI will also have an impact in Work Roles. For example:
- AI is a new technology that needs to be considered strategically to understand the impact it will have on an organisations goals and workforce.
- AI will continue to evolve and this means it will also need securing.
- AI is also a promising tool that can be used by many team members to improve their security work.
If you want to have a look at their recent change you can find their article here.
Access to the NICE Framework can be found here.
If you are interested in learning more about AI in cybersecurity, the NICE framework recommends some courses here.
Has the relative amount of Cybersecurity attacks increased over the years?
Cybersecurity attacks have definitely increased over time, specifically 650% since 2008, but that is expected, as tech becomes more and more adopted, we see an increasing size of the attack surface and as a result, an increase in the amount of possible attack vectors, and therefore incidents.
But that's a simple question with a very obvious answer. We should be asking much more specific questions, such as:
- Has the relative amount of attacks increased over the years?
- Do we have less incidents than we could have because of security controls implemented or just because attackers are running out of capacity to exploit everything.
These are the questions that Phil Venables highlights in a recent article he posted in the summer of 2025 that you can find here.
He also highlights some other important facts including:
- SMEs have a higher number of absolute security incidents, but only because there are more SMEs than there are large enterprises. If we look relatively, we would actually see that large enterprises have a higher relative security incident vs. number of large orgs that exist.
- The probability of a <$100M company experiencing an incident having doubled since 2008, but a >$100B company has dropped by a third since 2008. His reasoning is that the cyber poverty line prevents certain luxuries afforded to companies that can justify the cost vs. those that cannot and therefore have a weaker security posture.
Phil Venables is a legend in the industry. He is Google Clouds CISO and writes some incredibly insightful cybersecurity posts on his blog. If you are interested in a more holistic view of cybersecurity, I would highly recommend him as a source of reading.
This article was inspired by Cyentia 2025 Information Risk Insights Study which you can find here.
Cloud Logging for Security
As more and more of our technology shifts towards the cloud, there is an increasing need to monitor exactly what is going on in the cloud. It is not good enough to simply use the default cloud logging technology based on your CSP. Instead, your business needs it's own strategy to monitor it's cloud resources.
Unit 42 creates a detailed plan as to how to do that, in a recent article: Cloud Logging for Security. Below is a summary:
Control Plane vs. Data Plane
It is important to know the difference between the control plane and the data plane. Both do different things and therefore require their own unique logging strategy.
Data Plane - Provides the underlying functionality for each CSP service. This includes: Connecting into virtual machines, placing items into object-level storage, or creating a database.
Control Plane - Enables administration and management of resources within the CSP. This includes: Logging into a CSP console, Making API calls to modify resources, and creating new resources.
Where the data plane is where all the service functionality can be found, the control plane allows for the management of the service.
Security Information and Event Management (SIEM) Solution
Every organisation should look into getting a SIEM solution. One of the most popular SIEM solution is Splunk.
The goal of SIEM's is to collect all logging information into one centralised place. Whereas CSPs may have their own dashboards for logs, they are not specialised specifically for SIEM, and therefore a SIEM tool will have more functionality and more customisability.
Not only are SIEM's better at representing logs, but they also allow for logs from multiple CSPs, and even other security tools, which is perfect for large companies who have a large security arsenal and cloud sprawl.
Logging Considerations
As I mentioned briefly, different organisations will have different goals for logging, therefore they require a unique strategy. But there are some things to consider to help you build out that strategy.
Critical Business Functions
What are the systems, applications and processes necessary to ensure the availability of business operations.
Business Impact Analyses (BIAs) are a useful way of identifying and assessing the potential effects of disruptive events to critical business operations. They estimate financial and operation impact caused by disruptions. This is a good place to start, and a good guide to highlighting what metrics should be tracked. The below diagram shows how to determine overall logging criticality for a specific business function.
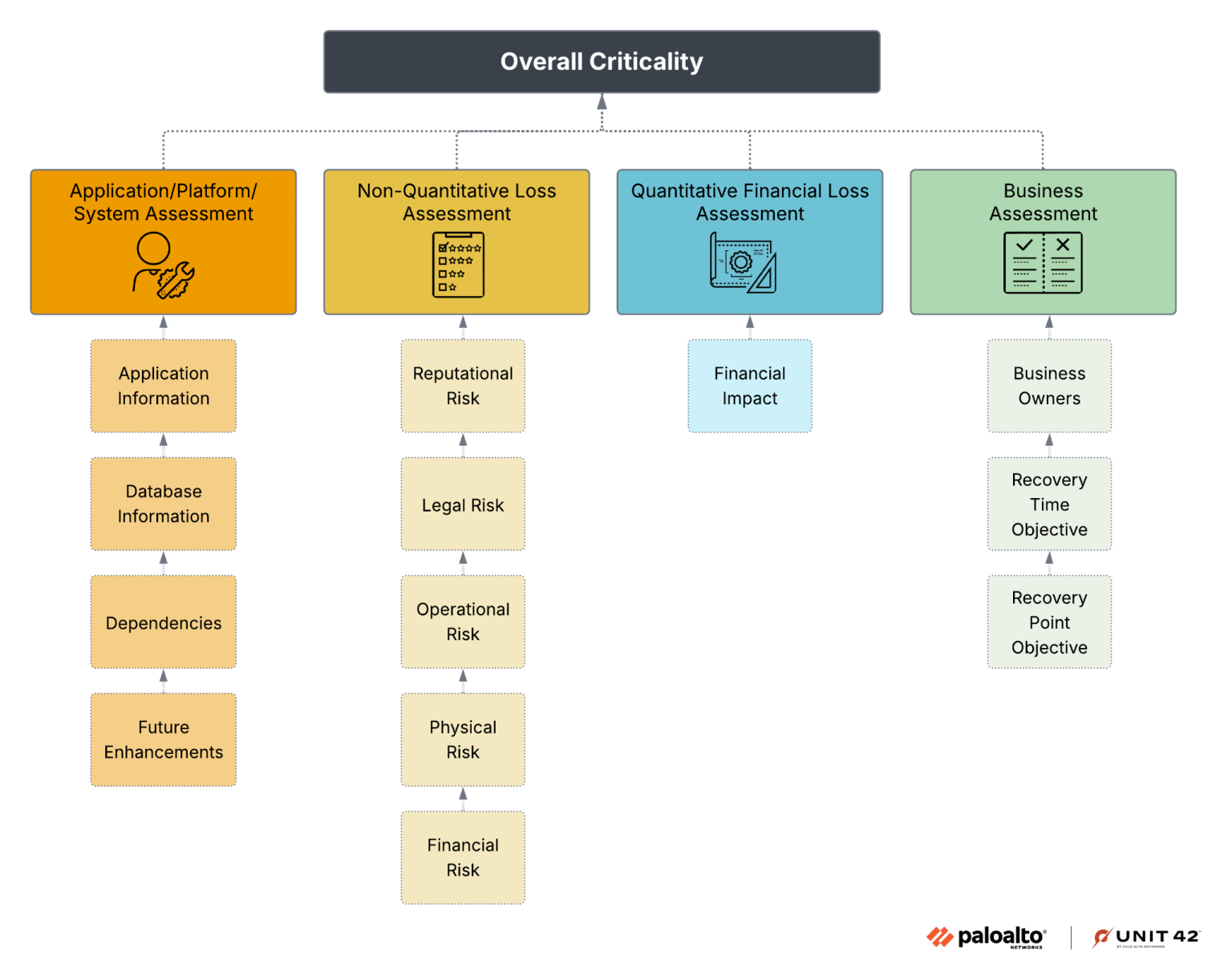
Once you have identified the critical business functions, you should focus on collecting the logs for them.
Regulatory & Data Requirements
Organisations will have to identify the regulations that apply to them based on the industry & country they are in. Some of the most common regulations that you probably have to consider includes:
- GDPR
- HIPAA
- PCI DSS
However, you should also probably compare your organisation with the NIST SP 800-Series frameworks, as they are a solid go to guide for how to build up the security in your organisation.
Security Operations Considerations
You should also consider the logs that are needed for your security team to function efficiently, and well. If your team is lacking the appropriate logs to investigate incidents, they are unable to learn, and therefore are still susceptible to the attack that caused the incident.
Cost Optimisation
Lastly, you need to work within your budgets constraints. If you simply cannot afford to log every detail, or maybe paying for a SIEM, you have to settle with what you do have and what you can get for free.
Have a look at your security controls, and have a set of priorities (these should be based on how good they are at securing your posture, and assign a budget accordingly. If you have enough budget for everything, great, if not, work with what you do have.
Logging Categories
There are many different logging categories, typically broken up by cloud service or functionality. Below is a summary of the main types, what you can log, and why you should log them.
Audit
Audit logs provide records of user activity and system changes. They typically give you insight into the control plane and are enabled by default in all major cloud providers.
AWS and GCP include identity-related logs here, while Azure separates identity logs into a dedicated category.
Compute
Compute logs give you visibility into:
- Management actions on compute resources (creation, deletion, modification)
- Activity and usage data from the compute environment itself
These logs cover both the control plane and data plane.
Network
Network logs provide visibility into both control plane and data plane activity, including:
- Firewall blocks and network filtering decisions
- Network flow information
- Configuration changes
Network logging can get expensive due to the sheer volume of data generated.
Secrets
These logs track activity around sensitive stored information, such as passwords, API keys, and credentials.
Events like creation, retrieval, modification, and deletion of secrets are critical to monitor.
Cloud-Native Storage
Object storage services also support logging for actions like creation, deletion, and modification.
This is extremely important if you rely on services like AWS S3, as object storage often supports core business functions.
Database
Databases hold large volumes of critical information and are central to most applications—especially those interacting with users.
Monitoring logs across both the control and data planes is essential to ensure security and operational stability.
Kubernetes
Kubernetes is a highly scalable platform for running applications across different environments, which is why it's so widely adopted.
Because Kubernetes plays such a critical role, it’s important to log both control plane and data plane activity, such as:
- Network traffic flows
- File system access
- Excessive resource usage
- Unauthorized lateral movement
Logging Table
If you are working on CSPs often and you need a way of tracking CSP services for specific logs, below is a table created by Unit 42.
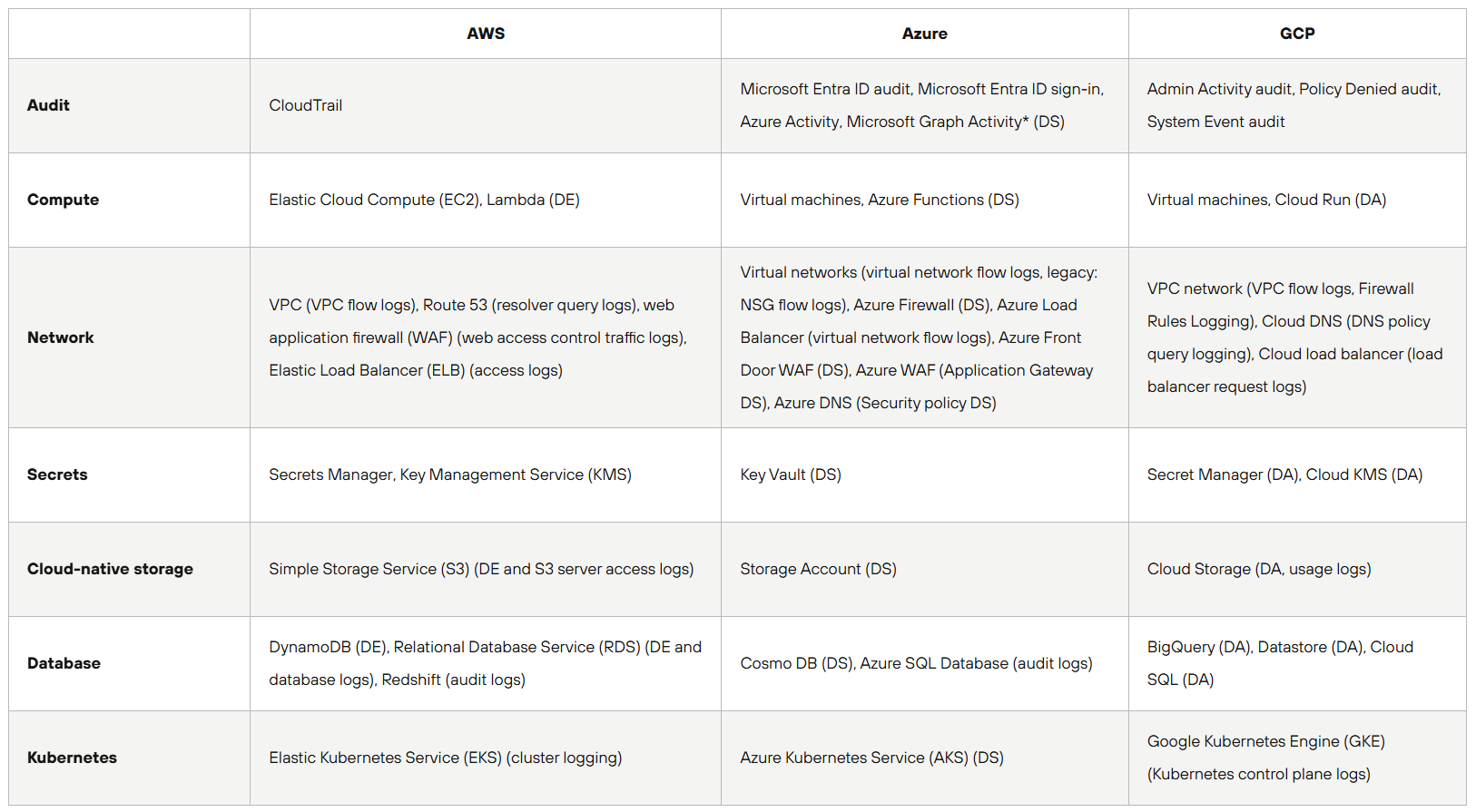
I would highly encourage you read the full article, there are so many helpful pointers for how to start the setup of your cloud logging, and plenty of resources, articles, and links that will answer every and all of your questions. You can find the article here.
Other Reading
- Google announced the first-ever verifiable quantum advantage using its Willow chip and the Quantum Echoes algorithm, achieving a 13,000x speedup over classical supercomputers for a real-world molecular modelling task. This breakthrough marks a shift from theoretical benchmarks to quantum applications, with results that are reproducible and scientifically verifiable.

Final Thoughts
If you've read through this entire article, thank you. Let me know if there is anything you want me to look at and explain, especially if you think it would help others out too.
Thanks for reading this edition of Security Diaries. My goal is to document the progress I make learning more about technology and cybersecurity, with the hopes of inspiring others, informing others, and show that I know what I claim to know.







