Security Diaries #7

Importance of Asset Management
An asset in cybersecurity is any physical or digital resource that holds value for an organization.
Surprisingly, 43% of small businesses fail to track their assets. There aren’t solid statistics for medium or large businesses, but it’s reasonable to assume the number would be even higher. Larger organizations often tweak the scope or requirements of an asset, sometimes making it appear more secure or valuable than it actually is.
Too often, asset management is treated as a minor, checkbox exercise—something completed just to avoid regulatory fines in case of a breach.
This mindset is dangerous. It ignores a fundamental principle of cybersecurity: how can you defend something if you don’t even know it exists?
Many security issues could be prevented simply by knowing exactly what you have to protect. With a clear asset inventory, you can:
Understand the true state of your security posture, identify weak points, and recognize what is already secure.
Build a more effective security program that addresses the issues uncovered in step 1.
Invest appropriately in the areas that actually need protection—no more, no less.
Asset management isn’t just about compliance—it guides your budget, informs your security strategy, and provides a clearer picture of your overall security posture.
Yet, despite these obvious benefits, many organizations still don’t see it as worth the time and effort.
Here’s an ideal approach to creating and maintaining an asset inventory:
Review all products and identify everything required for them to function. This includes SBOMs, infrastructure, administrative technology, data—literally anything necessary for the service to operate.
Establish a consistent routine to keep the inventory up to date. New product update? Update the asset inventory. New workflow or process? Update the asset inventory.
The advantages of maintaining a thorough asset list are too significant to ignore. Although asset management is taught as a core cybersecurity practice, complacency has turned it into a “nice to have” rather than a “must have.”
Underground AI tools used by Cyber Threats
GTIG AI Threat Tracker: Advances in Threat Actor Usage of AI Tools
Recently, Google has released a new threat intelligence blog talking about all the different AI tools being used by threat actors. There is a ton of information on this blog and would highly encourage people to read it, but one thing I would like to highlight is the different tools and their capabilities.
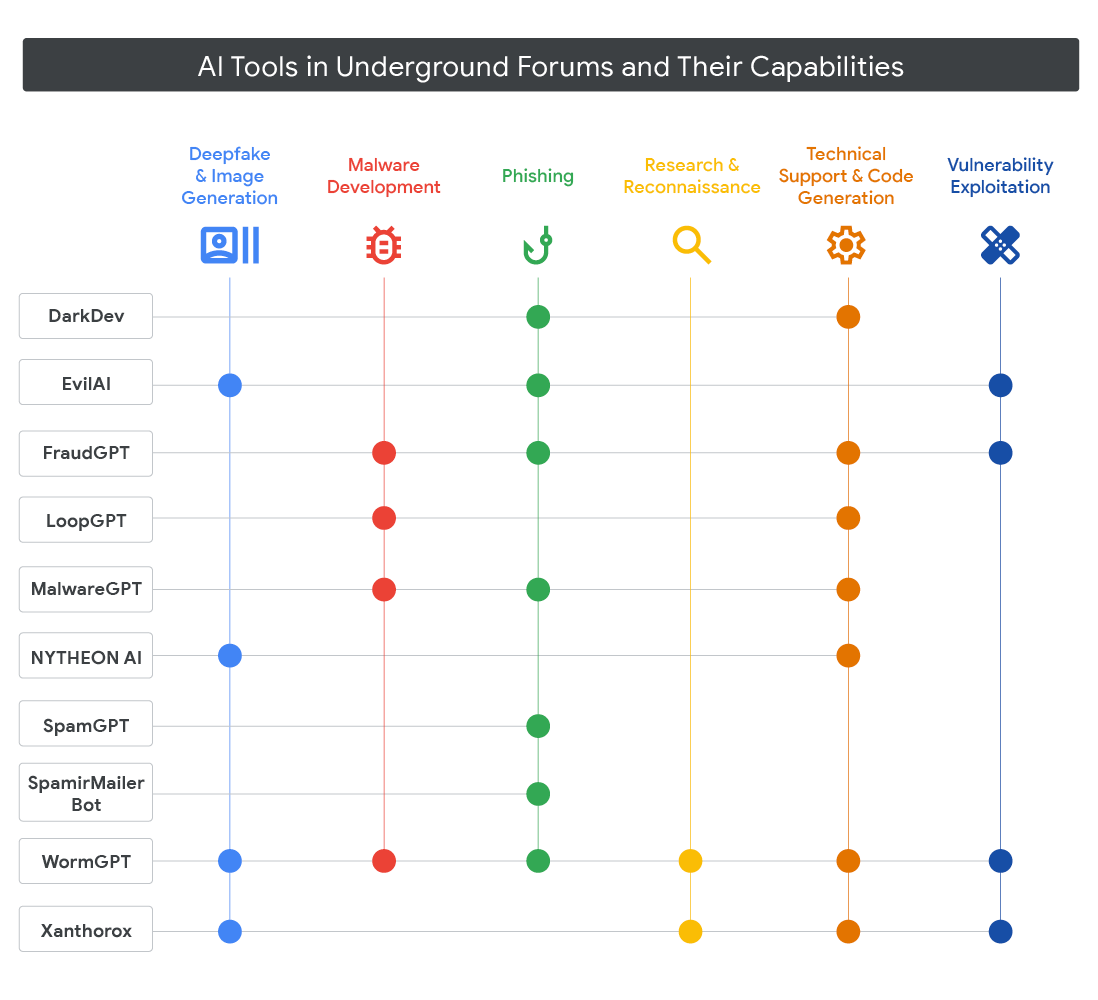
It just comes to show all the capabilities that can do, but from a harmful perspective. Hopefully this is used to grow awareness of all the malicious capabilities out there, so people can be more vigilant.Cyber Action Toolkit
With 1 in 2 UK small businesses identified a cyber attack last year and around 1 in 4 UK small businesses experienced a cyber crime, the UK has released a new toolkit that can be used by small companies with the goal of improving the cybersecurity posture for free. It is a recent government initiative with the hopes of reducing the amount of successful attacks that happen against small businesses.
The tool is split into 3 sections (Foundation, Improver, Enhanced) with a recommended completion time frame for each one. Each section has a checklist of things that should be completed to ensure the security of their business is as strong as possible.
Although it isn't something with strict validation requirements, it is a good toolkit to use for any business who is looking to up their security posture.
Cyber Action Toolkit
With 1 in 2 UK small businesses identified a cyber attack last year and around 1 in 4 UK small businesses experienced a cyber crime, the UK has released a new toolkit that can be used by small companies with the goal of improving the cybersecurity posture for free. It is a recent government initiative with the hopes of reducing the amount of successful attacks that happen against small businesses.
The tool is split into 3 sections (Foundation, Improver, Enhanced) with a recommended completion time frame for each one. Each section has a checklist of things that should be completed to ensure the security of their business is as strong as possible.
Although it isn't something with strict validation requirements, it is a good toolkit to use for any business who is looking to up their security posture.
Further Reading
- OWASP Top 10 2025 is out, with not much changing, but some interesting additions and moves.
- Meta recently reported that 10% of their revenue from Ad's comes from fraudulent sources.
- Are you interested to see which countries are passing AI laws? Well look no more, there is a world heatmap for exactly that.
- The EU has outlined what it seeks when procuring cloud services in its new EU Cloud Sovereignty Framework. The framework aims to reduce dependency on non-EU cloud providers and strengthen long-term resilience. It defines eight actionable sovereignty objectives, each assessed using a scoring system (SEAL levels 0–4). Higher scores indicate stronger alignment with EU sovereignty goals, helping determine eligibility and preference during procurement.
- The echogram attack that can be used to undermine AI guardrails even for modern systems
Final Thoughts
If you've read through this entire article, thank you. Let me know if there is anything you want me to look at and explain, especially if you think it would help others out too.
Thanks for reading this edition of Security Diaries. My goal is to document the progress I make learning more about technology and cybersecurity, with the hopes of inspiring others, informing others, and show that I know what I claim to know.




